On the 4th of April 2018, three members from Hepta Analytics formed a team to participate in the 24 hour Facebook/CMU-Africa Cybersecurity hackathon held at the Marriot Hotel in Kigali, Rwanda. 36 hours later, having not slept after hacking away all night, Yvonne, Rahab and I emerged winners of the top prize: An all expense paid trip to attend this year’s Facebook F8 conference in San Jose, California. This is the inside story of how we managed to pull it off.
A few weeks to the event, Yvonne and Rahab approached me with one simple question: Do you want us to take you to San Jose? “Uhhh, yeah” I replied. “Check your email and sign up for the Facebook cyber security hackathon then”. I complied.
Although not explicitly stated, I knew that they would leverage my cyber security knowledge and I their data science knowledge to build a security product that would continually better itself over time based on data and trends. This is the future of the cyber security field after all.
The day came and we strategically placed ourselves in a corner of the hacking room, away from direct AC contact, not too far away from the food and with lots of power sockets for all our gadgets. The importance of a good seating position in a hackathon can not be underestimated.
On the tables, we found the details about the hackathon and the judging criteria that would help us begin ideating. We looked through it keenly and discussed it at a high level while others munched away at the lunch. Only after we had a firm grip of the document did we proceed on to lunch where we discussed further.
After lunch, the ideating process continued with us filling a page with bubble diagram of the various themes and topics we could tackle. “The biggest industry-specific cyber security challenge in Africa” was the problem; and the solution had to be impactful, viable, original…and, of course, utilize a component of machine learning if we were to utilize the strengths in our team.
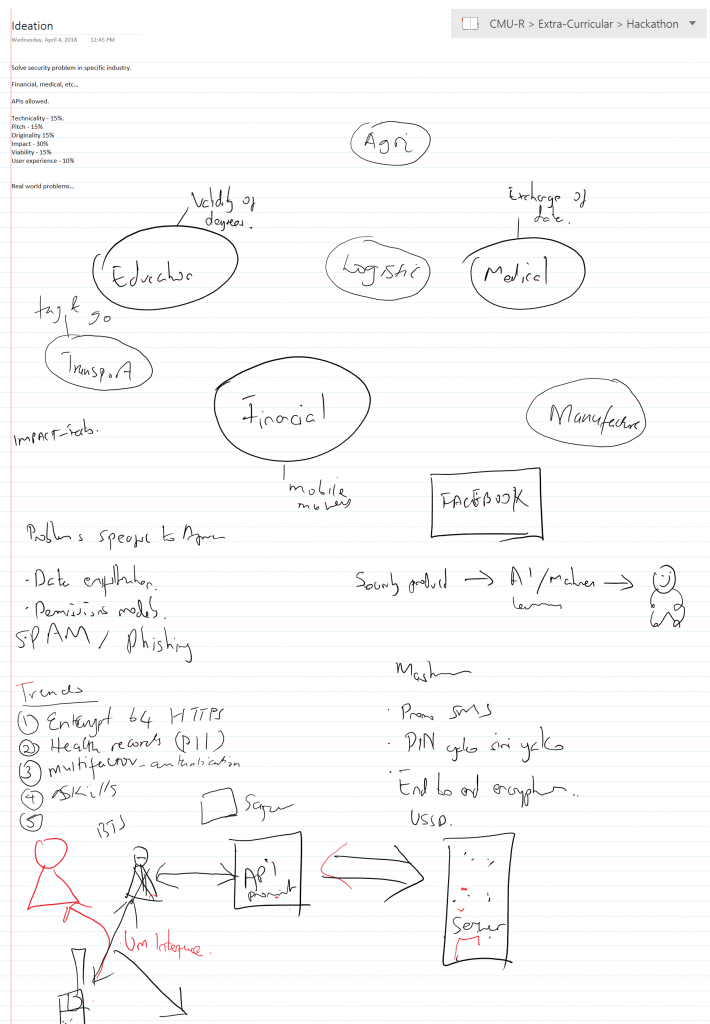
Hours passed and we still had nothing. We decided to change location to a cocktail table outside the room and later to the balcony and back inside. Still, the ideas didn’t flow. We got out of this endless loop and broke back to the beginning. We concluded that tackling a problem in the financial services sector would have the greatest impact and alas we had made some progress: deciding on the category. Then we agreed that the majority of users accessing financial services probably did so via feature phones and I explained to my members how insecure that channel was. Alas, our first idea was born: securing the USSD protocol (SUSSD).
Our plan was to develop an agent that could be installed at both the USSD gateway service provider and the clients’ server which would perform end to end encryption of data between hosts. This is because gateway providers often provide encryption but developers don’t meet the standard on their ends. We wanted to make life easy for those devs and offer encryption to them as a service.
Having bagged that as idea one, we felt we needed one more as a backup. We set a deadline of 5pm to get this done and kept rebooting back to the original question: “What is biggest industry-specific cyber security challenge in Africa?” Suddenly Rahab brought up the idea of identity theft and referenced the case of Sabina Chege – A Kenyan member of parliament who was recently a victim of impersonation. We continued to explore this challenge until we identified its root cause: social engineering – particularly via SMS’ and calls…commonly from Kamiti maximum prison in Kenya.
As we continued to refine the idea: Wilmer from Facebook approached us at the balcony asking for our team name. We immediately said: SUSSD! Then he asked for our app/hackname and since we were then discussing the Kamiti idea, we replied, “Kamiti”.
Now at our self-set 5pm deadline for ideation, we needed to choose an idea from the two and run with it. This was possibly the most critical decision we made the entire hackathon and consulted widely (Edwin, Cathy, Prof Tim, Vlad) to arrive at a decision. While securing a protocol was a novel idea and would impact millions, it didn’t touch people’s lives directly and most probably didn’t care how their data was being transferred…as long as they got service. At 7pm, wearrived at the decision to built Kamiti.
Having arrived at an idea, we relocated to an even quieter corner at the sleeping area to begin to design. We received advice from Cathy on how privacy of such an application had to be a huge consideration and embedded it into our design. On division of tasks, I would build the Android component (front end, permissions, etc) and the other members would work on creating a model and porting it to a mobile device.
By 11pm, I was still struggling with installing updates and setting up my environment (damn you Android Studio!) while Rahab and Yvonne had changed tact and decided against using a vector and instead passing the entire text through a model. Because we were now processing the entire text, it was at this juncture that we decided that we would not process any text messages from people in the user’s contact list for privacy reasons. This turned out to be key during judging.
Our integration meeting scheduled for midnight was postpone to 2am then to 3am then to 5am and ultimately after breakfast. “Sleep is for the weak!” Yvonne would say whenever any of us showed signs of fatigue. She would say this firmly fixated on her laptop with her Spotify playlist on full blast escaping sounds from her headphones while her head bobbed to the tunes.
When the model was finally ready, it was my job to integrate it but we also had the small matter of our presentation to figure out! We multi-tasked until we at least got the presentation done…but the integration still wasn’t working! We hoped that as the judges went round, our table wouldn’t be first so at least that would grant me some extra time to finish up. Our hopes proved true and I finally managed to get everything up and running (it turned out a few special characters were crashing the whole thing). Note to self: escape special characters properly!
Judge after judge came and while other teams slept in between, we spent time reviewing our previous presentation to a judge and refining it for the next. After the judging was over, I returned to the room to find we had been selected as the top four. While excited, I wasn’t really enthusiastic about presenting yet again in my tired state. It later turned out, neither were my teammates.
We huddled back into our corner and tensions were rising amongst my two team members which in turn affected my typically calm state. We had since gotten word that other teams were doing something similar and didn’t know the extent of their implementation which added to the pressure. Cathy and Edwin helped calm us down and offer some advice. For me, however, my mind was set: we would present exactly what we did to the other judges.
Our time to present came and right before we got on stage, I said to my team members: let’s just go out there, have fun and enjoy ourselves. I added “be confident, these are people you know after all”. The plan was Yvonne to kick us off, Rahab to follow, I to handle the demo and finally Yvonne to wrap up adding anything I might have missed. The plan worked perfectly and presentation went great with lots of humor, confidence and positive non-verbal cues from the audience.
We returned to our seats slapping high fives on the way back. We knew we had nailed it but didn’t want to “jinx it” so we stayed cool. In the evening, we were glad to be announced as winners!
I am grateful to CMU, Facebook and the entire team for putting the hackathon together and further grateful to all those who advised us including those at the conference and my colleagues back in Nairobi.
Also published on Medium.

Fantastic work from you and your team!!
I cant seem to wrap my head around how you guys managed to do all these in just hours……..